Basic Fortigate Configuration
Preface
Fortigate is a Next-Gen Firewall (NGFW) series released by Fortinet, has several variants from those that can be used for ordinary Internet Gateway (usually in branches, although in practice in some companies it is even used as a subnet gateway between Distribution and Core Layer), to the Data Center level that can serve hundreds of thousands of session per minute.
There are several things that need to be configured on Fortigate before it can be used as a gateway to access the internet, including:
- Direct Access to Fortigate;
- Interface Configuration that leads to the Internet;
- Configure default route (with and without SD-WAN);
- SD-WAN configuration for internet load-balance;
- LAN Interface Configuration;
- Policy Configuration.
Note
This configuration was done on Foritgate with Firmware v.7.0 and above. Most likely still applicable for FIrmware version v7.2, but it will be quite different from version 6. For the Firmware upgrade process, please check Upgrading Fortigate Firmware.
Procedures
Flowchart
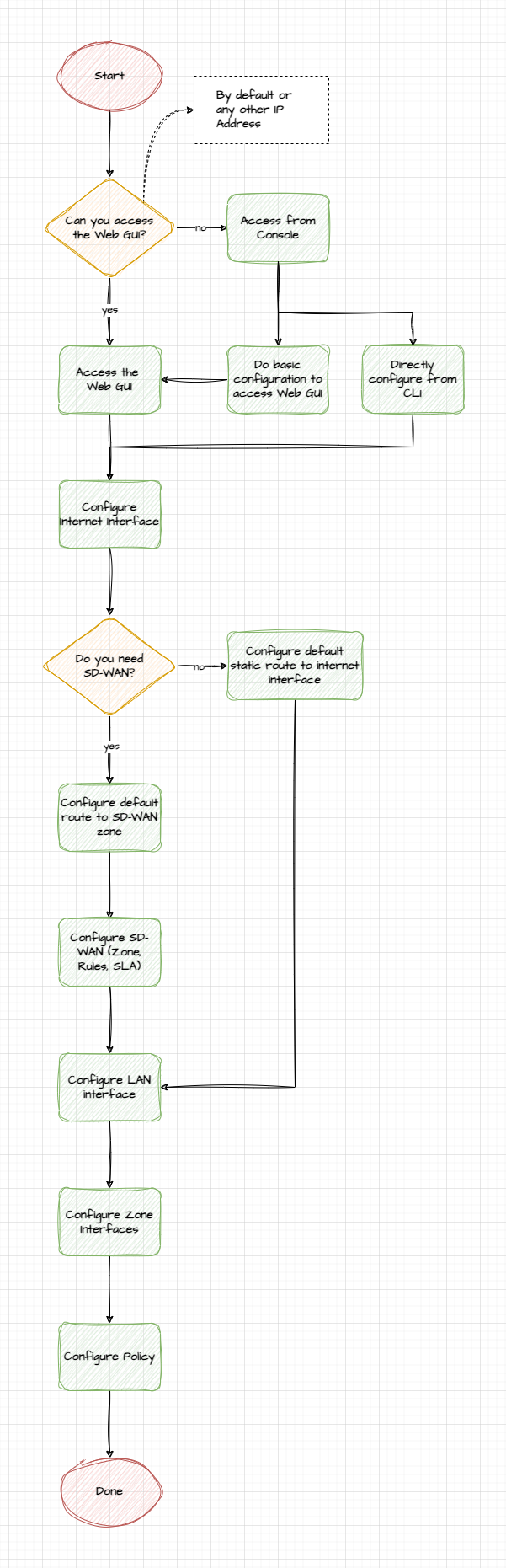
Case Example
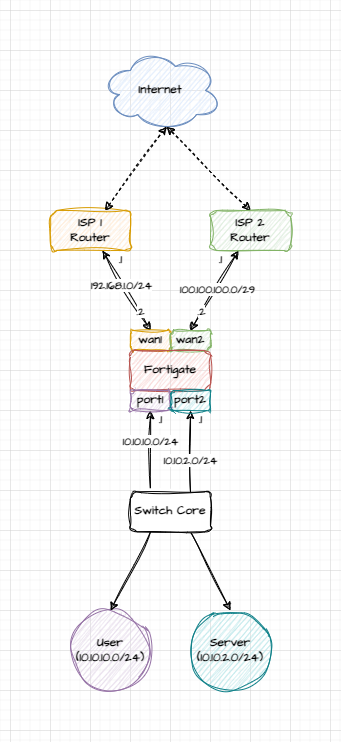
In this article, let’s assume that we are required to perform a deployment with the following information:
- There’s two ISPs: the first ISP provides broadband internet where we get a local IP address 192.168.1.x/24 by DHCP, and the second ISP provides dedicated internet where we have to configure a static IP address 100.100.100.2 on our router;
- There would be two different subnet: the first is for end user with the 10.10.10.0/24 IP addresses, and the second subnet is for Server which would have 10.10.2.0/24 IP addresseses;
- The end users need DHCP servers, while the servers will use static IP address;
- The server will always use the second ISP to access internet, while the first will always use the first ISP except when it’s down.
Direct Access to Fortigate
Via Web GUI
Fortigate generally provides initial access guidelines on a sticker on the body of the device. Initial access can usually be done by connecting our laptop with an RJ45 cable to the Port listed, changing the IP Network Interface of our connected laptop to 192.168.1.x (change x to any number except 99) with a subnet of 255.255.255.0, and then opening the URL [https://192.168.1.99](![[Pasted image 20240530101935.png]] ) through the Browser.
) through the Browser.

For the first access of a new device, you can usually use the user admin with a blank password. After the first login, we will be asked to create a new password.
Via Console
If we cannot access the device via the Web GUI, we can use an alternative access via the Console.
For Console access, we can use a common RJ45 Console cable that can be used for Switch/Router (usually in the form of direct RJ45 to USB, or RJ45 to Serial which is then converted again to USB). To access the Console device itself, you can use an application like Putty, although I myself use Mobaxterm because I’m used to it. The first user and password are the same as for the Web GUI, admin with a blank password.
At this point we can:
- do/check the interface configuration so that we can access the Web GUI from the IP Address of the interface;
- do the configuration itself through CLI in Console (not recommended unless you are used to it);
- perform a reset with the command
exec factoryresetto reset the Firewall configuration to default, so that we can access the Web GUI from the default IP address.
Interface Configuration that leads to the Internet
There are several forms of interface configuration that can actually be applied to the connection from Fortigate to the Internet, depending on the number of ISPs we want to use, whether there is a Switch in front of Fortigate or not, and whether we want to configure Fortigate into HA (High Availability) form or not.
In this case, let’s say we will do a standard configuration that uses two ISPs and Fortigate configured in non-HA mode, with a direct connection from the ISP router to Fortigate in the form of a single RJ45.
In some Fortigate models, there are ports that are named with WAN appendages (e.g. WAN1 or WAN2). These ports are actually just naming from Fortinet’s side, so they are no different from other ordinary ports, so it does not mean that we can only connect connections to the Internet on these ports (so don’t hesitate if for example we have more than 2 ISPs).
The first step that needs to be done is of course connecting the Router to Fortigate. Following our scenario, connect the first ISP to WAN1, and then the second ISP to WAN2.
Make sure again the Fortigate port where we connect the modem cable, then open the Port configuration in the Network → Interfaces → interface name menu.

For WAN1 configuration, we can simply select DHCP mode in Addressing Mode, then the interface will automatically get an IP Address from the router.

If we want to do manual configuration (as in the case where we get a Public IP and want the Public IP to be our own in our Firewall, like the second ISP in our scenario), just select manual and enter the appropriate IP Address configuration: 100.100.100.2/24.

[! Note] After configuring, do a test ping towards the gateway. This is arguably one of the most mandatory prerequisites at the beginning to ensure that Fortigate is able to be connected to the internet. To do a ping test, you can select the CLI symbol in the upper right corner, then in terminal mode, enter the following command:
execute ping {{ ip gateway }}As much as possible, make sure we can ping from Fortigate to Gateway before proceeding to the next step to reduce the headache ahead.
Configure default route (with and without SD-WAN)
The next step is to configure the default route. We can do this through the Network → Static Routes menu.

If we are not using SD-WAN, then the configuration is simply Create New route 0.0.0.0/0 towards the gateway IP Address.

If we want to utilize the SD-WAN function, for the interface, we can choose the name of the SD-WAN zone that we want to use to connect to the internet.
SD-WAN configuration for internet load-balance
Although the default-route configuration can be done without SD-WAN, configuring SD-WAN for the internet at the beginning can reduce the burden in the future, because later when we will implement the utilization of 2 or more ISPs, we can simply enter the interface connected to the second ISP CPE as an SD-WAN member.
Note
SD-WAN (Software-Defined Network) is a kind of next evolution of networking, where the behavior of a network is based on logic applied through software. In actual practice, SD-WAN requires an “Orchestrator” that controls all points in the network based on certain logic (usually in the cloud), but for our current case it is only limited to route selection based on SLA. Read more here.
SD-WAN Zone and Member Configuration
The configuration itself can be done in the Network → SD-WAN menu.

Fortigate generally immediately provides one default SD-WAN Zone that we can use: virtual-wan-link. We can delete the zone if the naming scheme is not suitable and then create a new Zone, but in this case we will directly use virutal-wan-link for the SD-WAN Zone that we will use for load-balancing connections to the Internet.
In the SD-WAN Zones tab, select Create New then select SD-WAN Member.

In the Interface section, select the interface that points to the Internet. In our case that would be WAN1 and WAN2. If our Interface gets its IP from DHCP, the Gateway section should populate automatically. If not, we can enter the gateway IP Address to the ISP there. Set Cost and Priority as needed, make sure the status is Enable, then select OK.
SD-WAN SLA Configuration

In the Performance SLA tab, we can create a kind of logic comparison that we will use later as a basis for selecting the route to be used.
There are several types of probing that can be used:
- Ping, where Fortigate will do a normal ICMP Request;
- HTTP Probe, where Fortigate will make HTTP requests;
- DNS Probe, where Fortigate will try to resolve DNS.
From the three probe modes, there are 3 types of values that we can later use: latency, jitter, and packet loss.

As a simple example, here we will try to do a configuration where we will pit which interface has the lowest latency Ping towards Google DNS (8.8.8.8), and then use the route on the interface with the lower latency value.
In the example image above, we can fill Name with a name of our choice (e.g. “Internet SLA” or “Google”), select Protocol “Ping”, and then enter the IP “8.8.8.8” in the Server section. For Participant, to simplify, we can simply select the required Interface, which in this case is the Interface pointing to the Internet/CPE ISP, and Enable the “Update static route” option if we want the Route to completely disappear when SLA fails.
SD-WAN Rules Configuration
The last thing to do is to set the Rules of the desired network behavior. This menu can be found in Network → SD-WAN, then in the SD-WAN Rules tab.

To create new Rules, simply select Create New, then fill in the required details.

For Name, you can fill it as necessary. Make sure to limit the characters that can be used for the Rule name.
For Source and Destination, this will be the “prerequisite” that determines which Outgoing Interface will be used when forwarding traffic.
For example, if we want only a certain Source (e.g. 10.10.0.0/16) to be able to access the internet through the first ISP (connected to wan1), we can make the following settings:**
- Name: LOCAL_TO_INTERNET
- Source Address: 10.10.0.0/16 (create Address if it does not exist);
- User Group: enter the user group if we also want to use user-based filters;
- Destination Address: because we want to specify the path to the Internet, for Destination Address we can select “all”;
- Internet Service: if we want this Rule to work based on Application and not IP Address, we can also select the Application that we want to set here. This is very useful for use cases where we want to separate traffic, for example we want Youtube and Zoom connections only through the second ISP.
For the Outgoing Interfaces section, there are several strategies to choose from:
- Manual, load-balance between Outgoing Interfaces will be done by failover, where the second Outgoing Interface will only be used after the first Outgoing Interface dies in the order we choose;
- Best Quality, Outgoing Interface will be selected based on SLA Performances that have been made before;
- Lowest Cost (SLA), Outgoing Interface will be selected based on the SD-WAN Member with the lowest Cost in the SD-WAN Zone. Outgoing Interface with higher Cost will be used if the Interface with lower Cost fails to meet the SLA Performance;
- Maximize Bandwidth (SLA), all Outgoing Interfaces that meet the Performance SLA will be used together in a load-balanced manner.
Interface preference and Zone Preference are useful if you only want to use a certain group of Outgoing Interface for this Rules.
For example, for Internet access, it makes sense to limit the Outgoing Interface selection to only those interfaces that point to the Internet. We can manually select those interfaces, or directly select the zone that points to the internet (“virtual-wan-link” earlier).
Now, for our case, you need to make the following Rules:
- Server rule to tell 10.10.2.0/24 sources to go through second ISP;
- End user rule to tell 10.10.10.0/24 sources to go through first ISP;
- A default rule where all sources is go through available ISPs.
For Measured SLA, we can choose the SLA that we have previously created.
Finally, just select the Quality criteria that we want to make a point of consideration in selecting the Outgoing Interface (unless you choose the Manual strategy), make sure Status is in the Enable position, and select OK.
LAN Interface Configuration

There are several interface configuration options that can be done:
- For the most basic configuration, we can directly attach an IP Address to the Physical Interface that leads to the LAN (such as Switch Core), for example “port1”;
- We can create a VLAN Interface on the Physical Interface that leads to the LAN.
Note
For configurations with even more flexibility, I really recommended to create a LACP configuration first to combine two or more physical interfaces into one. So that if an interface is damaged, we can simply change the members of the LACP interface.
To create a LACP Interface, from Network → Interfaces, select Create New, then when creating a new Interface in the Type section select “802.3ad Aggregate” and in the Interface members section select the interface you want to make a LACP member.
If we want to give the IP Address on the physical interface directly, you can just select the Interface that you want to use as a LAN connection in the Network → Interfaces menu. Meanwhile, if we want to create a VLAN Interface, from Create New, we create an Interface with Type “VLAN”.
For our case, we need to do configuration on two interface:
- For port1, configure its IP address to be 10.10.10.1/24, and enable the DHCP server;
- For port2, configure its IP address to be 10.10.2.0/24.
You can need enter the values of IP Address, Administrative Access, Receive/Transmit LLDP, DHCP Server, and Traffic Shaping according to your needs.
Connect the ports to its appropriate switch ports, and make sure the clients able to ping to the gateway.
Policy Configuration
Optional: Zone Configuration

To increase flexibility in Policy usage, you can use a Zone to cover multiple interfaces at once. To create a new Zone, from the Network → Interfaces menu, select Create New, then select Zone.
With Zones, we can group several different source interfaces into one group. For our example, we have 2 different interfaces, “port1” with IP Address 10.10.10.1/24 and “port2” with IP Address 10.10.2.1/24. We can put “port1” and “port2” into one Zone, for example we name it “internal-zone”.
Later, in Policy, we can use this “internal-zone” as a “Source Interface” for traffic coming from “port1” and “port2”.
Policy Configuration

To create a new Policy, you can do so from the Policies & Objects → Firewall Policy menu, then select Create New.
For example, if we want to create a basic LAN configuration so that it can access the internet, according to the configurations we have made before (LAN using Zone, and Internet using SD-WAN), we can fill in the values like this:
- Incoming Interface uses “internal-zone”;
- Outgoing Interface uses “virtual-wan-link”;
- Source we can use “10.10.10.0/24” and “10.10.2.0/24” (you can create a new Address Object if it doesn’t exist);
- Destination is filled with “all”;
- Schedule is filled with “Always”;
- Service is filled with “ALL”;
- Inspection Mode is filled with “Flow-based”;
- NAT in “enable” condition (because this is access to the Internet, for internal access it is usually not necessary);
- IP Pool Configuration select “Use Outgoing Interface Address”;
- Security Profile can be selected as needed;
- Logging Options, for Log Allowed Traffic, you can select “enable” and select “All Sessions” so that we can monitor Internet usage from the LAN;
- Finally, don’t forget to select “enable” in the Enable this policy option before pressing OK.
Testing Configuration and Monitoring
If we use the IP Address configuration directly on the Physical Address, we can do a test by connecting the laptop/PC to the Fortigate port that leads to the LAN.
If we use DHCP configuration, then our laptop/PC will get IP from Fortigate.
If not, then we need to configure the IP Address on the PC/Laptop, with:
- IP Address and Subnet Mask PC/Laptop are on the same subnet as the Firewall interface;
- Default Gateway with the IP Address of the Fortigate interface;
- DNS can be temporarily filled with public DNS such as Google (8.8.8.8, 8.8.4.4) or Cloudflare (1.1.1.1, 1.0.0.1).
After our PC/laptop has an IP Address, we can do some testing as below:
Client and Gateway Connection
From CMD/Terminal, ping the IP Address of the Fortigate interface. If it fails, some configurations that you can check include:
- Is the port connection between Fortigate and PC/Laptop on the correct port?
- Is the Network Interface on the PC/Laptop side active, and has the correct IP Address?
Client Connection to the Internet
From CMD/Terminal, ping the IP Address on the Internet. For example to Google DNS (8.8.8.8, 8.8.4.4). If it fails, there are some configurations that you can check:
- Default Route Configuration: make sure it is to the correct interface/SD-WAN Zone;
- SD-WAN Configuration**: make sure the Rules (source address, destination address, outgoing interface) are correct and the Performance SLA is running normally;
- Policy Configuration**: make sure the source/destination address, incoming/outgoing interface, schedule, and allowed services are correct.
In some case, there are instances where PC/Laptop can ping to IP Address (example: 8.8.8.8) but not to domain (example: google.com). For case like this, several points can be checked:
- DNS Server Configuration on the PC/Laptop Network Interface;
- Whether the PC/Laptop can connect to the IP Address of the DNS server;
- Whether the PC/Laptop can connect to the DNS server port (generally TCP/UDP 53).
Note
If we use the VLAN Interface configuration in Fortigate, to do testing we need a managed Switch that has VLAN features. Connect the VLAN trunk/tagging Port with the same VLAN ID as the VLAN Interface on the Fortigate side, then connect the PC/Laptop to another Switch Port that is set as an access/untagged Port with the same VLAN.
Conclusion
If all tests are successful, basically users and devices in the LAN network should be able to access the Internet.